Abstract
This page describes debugging issues when configuring Infinite BrassRing Platform SSO.
Experienced Identity Provider admins might have their own documented troubleshooting flows and procedures that are based on the system your organization is using. The processes on this page are provided for initial guidance.
Troubleshooting Initial Setup Issues
The following are suggested guidance to debug any SSO configuration at the initial setup:
If an error message is displayed on the browser page with any error codes, see SSO Single Sign-on Error Messages for suggested actions.
Check to make sure that the correct Infinite BrassRing Platform certificates are being used in the IdP system. For more information, see Configure your organizations Identity Provider.
Check validity and correctness of client provided Signing and Encryption certificates:
In Infinite BrassRing Platform Admin, select Menu → SSO → Inbound.
Select Show Details for the certificates to be checked.
Ensure the Issued by and Subject DN are verified by your organizations IdP admins.
Ensure the Start Date is not newer than the current date.
Ensure the Expiration Date has not passed.
If any of these checks fails, your organizations IdP administrators need to provide the correct certificate.
If a new metadata file of your organizations IdP is uploaded to Infinite BrassRing Platform, the entity ID of the client IdP system might be different in the newly uploaded metadata file. This requires the Login URL definition to be updated in Infinite BrassRing Platform by selecting Generate login URL.... For more information, see Configure Talent Suite Service Provider (SP) Inbound SSO.
Inspect SSO SAML communications (see "How to Obtain SSO SAML Communication Messages" section for guidance) for the correctness of the following attributes
In the AuthnRequest communication that is sent by Infinite BrassRing Platform to the Identity Provider system check the attributes listed. If any of these attributes are incorrect, review the SSO configuration in Infinite BrassRing Platform SSO Admin and take the corrective actions. Since these values might have been provided in your organizations metadata file, the metadata file might need to be updated and reuploaded to the Inboud SSO configuration menu. For more information, see Configure Talent Suite Service Provider (SP) Inbound SSO.
AssertionConsumerServiceURL attribute is Infinite BrassRing Platform's saml20 login end point. The value of this attribute defined in Infinite BrassRing Platform SSO metadata file AssertionConsumerService attribute.
Destination attribute is client IdP's saml20 login end point.
Issuer attribute is Infinite BrassRing Platform's saml20 end point. The value of this attribute defined in Infinite BrassRing Platform SSO metadata file entityID attribute.
In the Response communication sent by your organizations IdP system to Infinite BrassRing Platform
Destination attribute is client Infinite BrassRing Platform's saml20 login end point. The value of this attribute defined in Infinite BrassRing Platform SSO metadata file AssertionConsumerService attribute.
Issuer attribute is client IdP's saml20 end point.
StatusCode attribute is Success. This code is provided by the IdP system and is the most important place to check for the SSO failures. Your organizations IdP admins need to check the IdP's documentation to understand the cause of each failure code. For example, InvalidNameIDPolicy is one most common failure codes that indicates that the user identifier, NameID attribute in the Response, is not in the format as it was expected by the Infinite BrassRing Platform and should be checked at IdP to match the format and valid, not null, or blank. For more information, see Define NameID Format on the Configure Your Organizations Identity Provider page. It is also recommend to check the IdP systems event logs where there might be more information about the reason for the unsuccessful code.
NameID attribute within the nested Assertion and Subject tags has the user information that is being authenticated. The value that is sent in this attribute needs to match what's defined in the username attribute in Infinite BrassRing Platform User Management.
SignatureMethod attribute within the nested Assertion and Signature tags has "http://www.w3.org/2001/04/xmldsig-more#rsa-sha256" algorithm
Troubleshooting User Specific Issues
Check to make sure that the user is provisioned, active, and SSO Enabled in Infinite BrassRing Platform
Confirm that the users have matching username in Infinite BrassRing Platform as the username sent in the SAML response NameID attribute
Ensure that 2-Factor-Verification is disabled in Infinite BrassRing Platform for the user in User Management. For more information, see How to Configure 2-Step Verification.
Troubleshooting Previously Working SSO Issues
Check to make sure the IdP certificates are still valid.
In Infinite BrassRing Platform Admin, select Menu → SSO → Inbound.
Select Show Details for the certificates to be checked.
Ensure the Expiration Date has not passed. If it has your organizations IdP administrators need to provide the correct certificate.
Check to make sure Infinite BrassRing Platform certificates that are used in the IdP system are still valid.
It is possible that the Infinite BrassRing Platform certificates have been refreshed. For the latest metadata files, that contain the certificates, see Configure Your Organizations Identity Provider.
The IdP admin needs to verify the certificates in the IdP system.
When Infinite BrassRing Platform certificates are approaching their expiration date, a notification is being sent to the clients with the instruction on when and how the new certificates can be obtained and when they become effective.
Communicating with Infinite for SSO Support
There are two types of error that can be encountered when configuring SSO in Infinite BrassRing Platform.
IdP errors can only be fixed by your organizations IdP administrator. The Infinite support team cannot support IdP issues such as the error in the sample image:
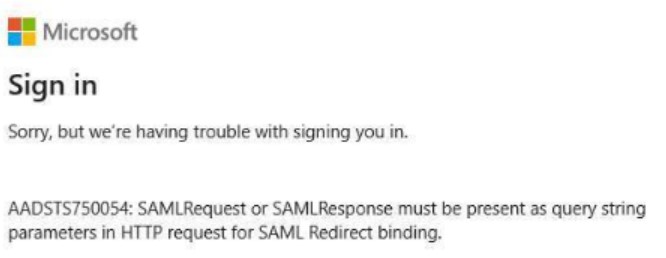
Only Infinite BrassRing Platform errors can be addressed and supported by the Infinite support team. If the error looks like the sample error in the image, check the SSO Single Sign-on Error Messages page to see possible solutions for the error. If any of the processes on this page do not help to solve the SSO issues and Infinite support team assistance is required, open a support ticket.
Ensure that the following information is included the support ticket where possible:
Describe if this is an initial setup issue.
Describe if the issue happening to only few users. If so, provide the usernames of the affected users and describe whether SSO worked for these users previously or not.
Include a screen capture of any errors.
Include the date and time stamp if they not available in the screen captures.
Include a SAML Trace. For more information, see How to Obtain SSO SAML Communication Traces.
Include any errors that might be logged in the IdP system
How to Obtain SSO SAML Communication Traces
The SAML trace contains important values for the key SAML attributes and greatly helps teams to debug the issues. There are two methods for obtaining SSO SAML communication for troubleshooting:
Collecting SAML Trace by using a browser plug-in. This is usually the easiest way to collect SAML traces by installing one of the suggested add-on SAML tracers:
SAML Tracer for Firefox
SAML Devtools Extension
SAML Chrome Panel for Chrome
Fiddler for Internet Explorer
To collect SAML Trace:
Open a new cache cleared, incognito, or private browser window.
Open the browser addon.
Go to the Infinite BrassRing Platform Login page.
Select Existing employee? Log in here.
Log in to the IdP after landing on the IdP page.
Both the SAML Authentication Request from Infinite BrassRing Platform to client’s IdP and the SAML Response from client’s IdP to Infinite BrassRing Platform should be logged by the SAML Tracer addon and can be used for further analysis.
Manual SAML Trace collection. If your organization cannot use any of the suggested plug-ins:
Open a new cache cleared, incognito, or private browser window.
Go to the Infinite BrassRing Platform Login page.
Open the browsers Network console , which can be found in the browser's developer tools or more tools menu item.
Verify the preserved log option is checked.
Select Existing employee? Log in here.
Log in to the IdP after landing on the IdP page.
There should be two login traffic logged in the Network console: one from Infinite BrassRing Platform to the IdP and one from the IdP to Infinite BrassRing Platform.
Select the login traffic from Infinite BrassRing Platform to the IdP.
In the Headers tab, locate SAMLRequest in the headers section and copy the value of the entire SAMLRequest that is base64 encoded.
Open a new tab and go to https://www.base64decode.org/.
Paste the copied SAMLRequest value in the Decode from Base64 format section.
Select DECODE.
Copy and paste the decoded content to a text editor for further analysis.
Select login traffic from the IdP to Infinite BrassRing Platform.
In the Headers tab, locate SAMLResponse and copy the value of the entire SAMLResponse.
Open a new tab and go to https://www.base64decode.org/
Paste the copied SAMLResponse value in the Decode from Base64 format section.
Select DECODE.
Copy and paste the decoded content to a text editor for further analysis.