Abstract
Enabling Single Sign-On (SSO) for the Infinite BrassRing Platform establishes authentication between the client system and the .
Setting up SSO
Setting up SSO for Infinite Talent includes the following steps:
Establishing trust by configuring inbound SSO. This step includes the exchange of security certificates that establish authentication trust between the client system and Infinite Talent.
Enabling the SSO identity source by configuring the login process for client users when they access the Infinite Talent.
Note
Administrators must complete the configuration of Inbound SSO before they enable and configure Identity Source.
Configure users for the Infinite Talent. Infinite Talent Solution Administrators complete this task.
Federating the Customer Environment with Configuration Data of the Infinite Talent Service Provider (SP)
Abstract
Configuring Single Sign-On (SSO) for the Infinite BrassRing Platform requires the configuration of Inbound SSO. Inbound SSO requires the exchange of security certificates that establish authentication trust between the customer system and .
Federating the Customer Environment with Configuration Data of Infinite Talent Service Provider (SP)
In order to federate the client environment with the configuration data of Infinite Talent Service Provider (SP), you need to pass the SAML metadata file of the Infinite Talent SP to the client.
Note
Only Infinite BrassRing Platform Administrators with the role of SSO Administrator are allowed to configure Inbound SSO and to manage certificates.
Getting SAML Metadata File of Infinite Talent SP
SAML metadata is the data that describes the information that is needed to communicate with a SAML endpoint. For example, if Identity Provider (IdP) X wanted to allow Service Provider (SP) Y to request SAML responses, IdP X would share its metadata with SP Y and vice versa. Some of these pieces of information include:
The services that are available at each endpoint
The addresses to use to access the endpoint services
Any certificate, and/or signature information
Note
Note that there are different versions of the SAML metadata file of Infinite Talent, one for each environment available.
Metadata is implemented in XML and does not contain any sensitive material, so signing metadata is optional.
Refer to the metadata from various environments to use for SSO implementations as follows.
SSO Metadata - Staging
Abstract
At this present time, the valid SSO Metadata - for Stag-US is listed in this document. As noted in the Frequently Asked Questions section of this guide, SSO Metadata certificates for each Infinite BrassRing Platform environment do expire and do need to be replaced on the date and time of expiration. Infinite BrassRing Platform's existing SSO metadata certificate must not be removed before the certificate expires. You will be notified prior the expiration date when to replace your Stag-US certificate.
SSO Metadata - Staging
This Stag-US metadata certificate is the NEW metadata certificate. Use this certificate in your Stag-US environment.
<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20">
<md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGujCCBaKgAwIBAgIJAK5MyG8QSaPyMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MTgyOFoXDTIzMDgzMDE1MTgyOFowJTEjMCEGA1UEAxMaaWJzc29zaWduLnN0YWdlLmtlbmV4YS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDQ5tv1LSAVMHA/YjveGjqXCl8sJ4OjmMjcffnYzUii3Oq1ItwF+9cT9690itU/drfLK7o7Rr0Hjw26lACsR94eMHTCgU6+38wN/4a/tsw8kMaBBuInHgB0BCHiZ0xGBZkZx/JH/e5AYU9uZC738Pmubx9mezczgX7ixCv0e8/qBdJ4xVT/DKbZJaytzEqimTzU4YfGNxDV/bXfVkrq655r2n6WUEhK3Q7JftbXg63Ag+inTQOUs6zXtt3ec0/GausGypN/dm5zh7SRJ8aTHLYrg3nEd9YX7N9kCVGG81nSwpKcEerc/LbQ2+5eIynS3IVVfHfyNE27p487FwVRIGBDAgMBAAGjggNbMIIDVzAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAOBgNVHQ8BAf8EBAMCBaAwOAYDVR0fBDEwLzAtoCugKYYnaHR0cDovL2NybC5nb2RhZGR5LmNvbS9nZGlnMnMxLTQ0MjQuY3JsMF0GA1UdIARWMFQwSAYLYIZIAYb9bQEHFwEwOTA3BggrBgEFBQcCARYraHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzAIBgZngQwBAgEwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5nb2RhZGR5LmNvbS8wQAYIKwYBBQUHMAKGNGh0dHA6Ly9jZXJ0aWZpY2F0ZXMuZ29kYWRkeS5jb20vcmVwb3NpdG9yeS9nZGlnMi5jcnQwHwYDVR0jBBgwFoAUQMK9J47MNIMwojPX+2yz8LQsgM4wRQYDVR0RBD4wPIIaaWJzc29zaWduLnN0YWdlLmtlbmV4YS5jb22CHnd3dy5pYnNzb3NpZ24uc3RhZ2Uua2VuZXhhLmNvbTAdBgNVHQ4EFgQUVVUnxVgtih97mQZIPQ8w7FkflQcwggF+BgorBgEEAdZ5AgQCBIIBbgSCAWoBaAB2AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9VHUMAAAQDAEcwRQIgO1aTDG1hmCfufQmJ5yjHbe4FJZ2SL+NC0sxoVDnxHWoCIQC3CQXuN257eYMZiSyAOnyBBn3Lg4BDwNpjclDCWvrIRwB3ADXPGRu/sWxXvw+tTG1Cy7u2JyAmUeo/4SrvqAPDO9ZMAAABgu9VHqkAAAQDAEgwRgIhAKTBMG8pfizulvTrI1GKkZP5y2xuQjapBQGeVqysD73iAiEAmp/8vm3oSUjC3FGtaohsEkCUXUlG9zJoaEWcSlAhRdkAdQB6MoxU2LcttiDqOOBSHumEFnAyE4VNO9IrwTpXo1LrUgAAAYLvVR8aAAAEAwBGMEQCIGlwb/Of1e/ouJzv8rlkOZmmp6o5qpnFJ8ERtJU37fG9AiB2CwrcIt0eQTPBREeK5CuOpvYA4EE5+z6JquX1/Se7MTANBgkqhkiG9w0BAQsFAAOCAQEAIEioFruyw9Ve21jvLh/vrIICDqLNKBlDive9CtvLSQJIcDYn9xhsq1+OVUBed1M4TULsYDx4Qnuv+gfjpsH2rLzK0y6jDVJPYhqXnnc28wtDdqdLYTkszxGTAY63d04zmyzuJCJ9gcs7KpVIOfN/E9280ZARgJl5e49drLF5m+TqQxRabb+l0pW8tmHJ2BAFKBVD7EVetH/FEcOstvLDod97U/0SZptMUbGAY1N6LiqWIJI4iNSc1fffn5xaPYloo1cAGdRXvJU36P4fFb3GctQ3x41gID95Aiut2AhTrXwDvLRf6OsyukPIM1BNZ7Scs0Zk0dHf/njzdArYe40Vrg==</X509Certificate>
</X509Data>
</KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGxDCCBaygAwIBAgIJAJ4yar8MbKMwMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MjAwOFoXDTIzMDgzMDE1MjAwOFowKDEmMCQGA1UEAxMdaWJzc29lbmNyeXB0LnN0YWdlLmtlbmV4YS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCYfMatFNuSY03qlImIc9UFtSuvQowka6cIbGH/TnRkSy4CBYbQEOtfthQp1Wu4uo4Za7aD7vUpKjxtXbEd6irvptAtY0NMBwOkJZfQtymDFZ9zJq7U5aHnBD//m3FZCGg/5z+XdAxVfKMBk0WTzaVPm2/8pjgbLvKOgpr5iHIfg72Ywwz98fjz+LN2qlsg0tlv/jKaM6g8WQEFqjzao7vZweT/BNWwI6ORh45cGCTEKCg/0Mq2DlUZGXAfHfo/ddgNieqC6Izi+44gg9fx0UpMVr8PO5DFjm3iJCgJvtqnvSJhGyf0lbExoL/s27cEqoEqmIaFYaayaMCwWHqqc6qHAgMBAAGjggNiMIIDXjAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAOBgNVHQ8BAf8EBAMCBaAwOAYDVR0fBDEwLzAtoCugKYYnaHR0cDovL2NybC5nb2RhZGR5LmNvbS9nZGlnMnMxLTQ0MjQuY3JsMF0GA1UdIARWMFQwSAYLYIZIAYb9bQEHFwEwOTA3BggrBgEFBQcCARYraHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzAIBgZngQwBAgEwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5nb2RhZGR5LmNvbS8wQAYIKwYBBQUHMAKGNGh0dHA6Ly9jZXJ0aWZpY2F0ZXMuZ29kYWRkeS5jb20vcmVwb3NpdG9yeS9nZGlnMi5jcnQwHwYDVR0jBBgwFoAUQMK9J47MNIMwojPX+2yz8LQsgM4wSwYDVR0RBEQwQoIdaWJzc29lbmNyeXB0LnN0YWdlLmtlbmV4YS5jb22CIXd3dy5pYnNzb2VuY3J5cHQuc3RhZ2Uua2VuZXhhLmNvbTAdBgNVHQ4EFgQU2/6qp8LpqJD5aEIPUFmZtoNgCg8wggF/BgorBgEEAdZ5AgQCBIIBbwSCAWsBaQB3AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9Wp2IAAAQDAEgwRgIhAI++D8ZOGmhaH/tVhLIR8k9EnNcxRhKaMV2QvMu3sJ22AiEA96W2+k+kAg0RxAl3VSXs6mYqEVOzcLuUE9ANCXvVFYsAdgA1zxkbv7FsV78PrUxtQsu7ticgJlHqP+Eq76gDwzvWTAAAAYLvVqi1AAAEAwBHMEUCIQC8bNf5sWlZGN68tTWYe1yKmHs7kQWLcfZ+2qwEPO3eMQIgQNGQTAN23wLnd7l+R9RwXBjz2jNoSfNBmnFuj/8Hvi0AdgB6MoxU2LcttiDqOOBSHumEFnAyE4VNO9IrwTpXo1LrUgAAAYLvVqkxAAAEAwBHMEUCIF82mX7c2tp/o8o2fEkAe6+CyHmtgwP6DazHlyF2tXBUAiEA+H4iylGfr0qjovycWmao6isexO+vq794HbIuruJJsYYwDQYJKoZIhvcNAQELBQADggEBAEDKaOdFz0DNNKUAMmy5ZYfr+T3qQDtPex6LdeNCzykNox0QXmg6LsnKu0QpsdxK0kN1SB40OqqWd+1TkagXiESsYocOILuspoKHyNit7Drfu3DKZHYOUqIfycn43ijipEU5g1d1fLipODRoHg5JY/XrYBouRBQ7Lh3WrTs07OKagUc6Cv2YSQC0+JQ4pL8mxpDNszYuCTsGjkzEvVJfy+MpKgK0FM0VprJncxghWtl19FNAVotKi7lztn+6Uae24Y0OXrfSM2PNtcujS2z1A/W6LC3zKETIPyVmEOdnLIyRPGPJVCGnYXRdZt942syrcPvAeQ7yxr/22+thNOrN/5s=</X509Certificate>
</X509Data>
</KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
</md:KeyDescriptor>
<md:ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap" index="0" isDefault="true"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/login" index="1"/>
</md:SPSSODescriptor>
<md:Organization>
<md:OrganizationName xml:lang="en">Infinite BrassRing Platform - Stage</md:OrganizationName>
<md:OrganizationDisplayName xml:lang="en">Infinite BrassRing Platform - Stage</md:OrganizationDisplayName>
<md:OrganizationURL xml:lang="en">talentsuite.infinite.com</md:OrganizationURL>
</md:Organization>
</md:EntityDescriptor>
SSO Metadata - US Production
Abstract
At this present time, the valid SSO Metadata - for US Production is listed in this document. As noted in the Frequently Asked Questions section of this guide, SSO Metadata certificates for each Infinite BrassRing Platform environment do expire and do need to be replaced on the date and time of expiration. Infinite BrassRing Platform's existing SSO metadata certificate must not be removed before the certificate expires. You will be notified prior the expiration date when to replace your US Production certificate.
SSO Metadata - US Production
This Prod-US metadata certificate is the NEW metadata certificate. Use this certificate in your US Production environment.
<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://2x.kenexa.com/sps/inboundSSOProd/saml20">
<md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGyDCCBbCgAwIBAgIJAJOajSjeHOqiMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MjI1NVoXDTIzMDgzMDE1MjI1NVowKjEoMCYGA1UEAxMfaWJzc29zaWduLnByb2R1Y3Rpb24ua2VuZXhhLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMWo2EUGbdxrDDjuYlrYjmydQLNHVb5UITFCmS2fGB7zvNOTGl+mKHdBD8NUYBL+wMzIcRsBaK6vOs1SeKGqKTMUCBFthCBF8QnLrr4RO1cmd8+q7ABRs/cKxUB/CrgxoPzQozx+PhsZF7VuTjLamdpYRwNwO78b7M0sXeUMeJ8PGzO6hR8lIiS+v0z6LBjnoaSFfCuZF2Os968EwuP2bGIGgeBMv1S+5LYpXDidBORBhDInayj3BcTNOQeK+36z5a7CBespBVmFjp0GMU1nlhe+Mf+xJ8rtoe5iwMdqUXc+at6G2D5kWJtbgXvz7S1hOMWNTyt9WrUrRCGXYcsSW9kCAwEAAaOCA2QwggNgMAwGA1UdEwEB/wQCMAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA4GA1UdDwEB/wQEAwIFoDA4BgNVHR8EMTAvMC2gK6AphidodHRwOi8vY3JsLmdvZGFkZHkuY29tL2dkaWcyczEtNDQyNC5jcmwwXQYDVR0gBFYwVDBIBgtghkgBhv1tAQcXATA5MDcGCCsGAQUFBwIBFitodHRwOi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvMAgGBmeBDAECATB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmdvZGFkZHkuY29tLzBABggrBgEFBQcwAoY0aHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5L2dkaWcyLmNydDAfBgNVHSMEGDAWgBRAwr0njsw0gzCiM9f7bLPwtCyAzjBPBgNVHREESDBGgh9pYnNzb3NpZ24ucHJvZHVjdGlvbi5rZW5leGEuY29tgiN3d3cuaWJzc29zaWduLnByb2R1Y3Rpb24ua2VuZXhhLmNvbTAdBgNVHQ4EFgQUQyXN12eXD37/++4xfxA5ldSZkQcwggF9BgorBgEEAdZ5AgQCBIIBbQSCAWkBZwB2AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9ZMBYAAAQDAEcwRQIgMWbwiy2xYUU4TTg4Odxmf5E8JZ5ly2Unu0NEz92c1W8CIQDeLtjQA07cLji2AxsEIYXDK9nrKj6HK8ud9+rFihdxtAB2ADXPGRu/sWxXvw+tTG1Cy7u2JyAmUeo/4SrvqAPDO9ZMAAABgu9ZMVoAAAQDAEcwRQIhAMUlfyvAm0FD+EIMIsyGp7axRAMEMQtvemTk41ZtsJ9/AiA9doxaz0lXnEvm0S1DEpb3wmXAtC6rOWRpK4PalpBQTAB1AHoyjFTYty22IOo44FIe6YQWcDIThU070ivBOlejUutSAAABgu9ZMdIAAAQDAEYwRAIgdaNZastV14HqMqB+jA+WFY45cxF/EP0ar/RKsLqeJPoCIDj9TmdoaTX7GH/kXxq2W+mACkLv20NYJDikl+j7bag5MA0GCSqGSIb3DQEBCwUAA4IBAQBF+D7fRlu2xhdxA2qbll7647foDHH8JVGPPqxO6BCQ8iwwn30qTHtbJZvOiEyUVgGWGnKB8wuPtp/rcIaVZ2DA6cmNeLK0Czqlf6MvnrlZzwyBTSSqB6Br3FQPEXLkG5MAVEMLwCDVGHAvhraYpf+mA36hZZuxMXPmlPz3iYg2tWN8XWHWT0YhYKiTt/lHBRYOOxIeTGdlzjz6haXfAxyj0Lz3IZIIRu9NwwCf0bQWoksqKUGr/pJrz96HbH36p3WjzJmoHaKo9yLpM8nF6N1iSS3wcNckHZiwswM2ApJcz8QmHir/P7Xm442KLoPdQ0L7sW7RaM4QNXiquesomsRO</X509Certificate>
</X509Data>
</KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIG0jCCBbqgAwIBAgIJAKcV08ucXJXlMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MjExOFoXDTIzMDgzMDE1MjExOFowLTErMCkGA1UEAxMiaWJzc29lbmNyeXB0LnByb2R1Y3Rpb24ua2VuZXhhLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOI255d42LIMjGGN+fVQpSq+j89ylkZsvVPEyDftqqAc1LEzBB1NmtCTPVMvvA3ctqRs9AHoU8QM/8kR95VK2ArkaI0yXvcBm3gjtOqEhUBQCar4DE8/SxCLnR9HG6OjwnCqV5Fg1RqHFyGAgBd3sxa0MKVkEHu2nmhbTjs+Ttv2E3rqlHTgQLm7tX7iKJ0VUrkG6Ece7z4jXbMtfrVmrEFBJeJx3stKB2RnN8ktbFuHfg8K8jgxwO2+PiB2Jon+rhEfTfv0Bb9Dmqn4xi/UEYOPUGM5wSVsHHLAUcuFc+EaS0pD9S8GTdT6qKee0V+mgRDVphKQXgGUcjZinxjgs/8CAwEAAaOCA2swggNnMAwGA1UdEwEB/wQCMAAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMCMA4GA1UdDwEB/wQEAwIFoDA4BgNVHR8EMTAvMC2gK6AphidodHRwOi8vY3JsLmdvZGFkZHkuY29tL2dkaWcyczEtNDQyNC5jcmwwXQYDVR0gBFYwVDBIBgtghkgBhv1tAQcXATA5MDcGCCsGAQUFBwIBFitodHRwOi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvMAgGBmeBDAECATB2BggrBgEFBQcBAQRqMGgwJAYIKwYBBQUHMAGGGGh0dHA6Ly9vY3NwLmdvZGFkZHkuY29tLzBABggrBgEFBQcwAoY0aHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5L2dkaWcyLmNydDAfBgNVHSMEGDAWgBRAwr0njsw0gzCiM9f7bLPwtCyAzjBVBgNVHREETjBMgiJpYnNzb2VuY3J5cHQucHJvZHVjdGlvbi5rZW5leGEuY29tgiZ3d3cuaWJzc29lbmNyeXB0LnByb2R1Y3Rpb24ua2VuZXhhLmNvbTAdBgNVHQ4EFgQUmHDSiM5BYFwSlqj1GshcfqT0UXswggF+BgorBgEEAdZ5AgQCBIIBbgSCAWoBaAB2AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9XtiAAAAQDAEcwRQIgGhRJLHt2LbLDVTTjhmRHefEtASSbS8bbgDoak9F5O9sCIQChpUiVRuJlC/Y87Lb+npGd1fQMIwXm017vVJ/YSC9zfQB2ADXPGRu/sWxXvw+tTG1Cy7u2JyAmUeo/4SrvqAPDO9ZMAAABgu9Xt18AAAQDAEcwRQIhAKxuwOPGc8SAde8MNLFD3s1Jh/377HVqUk60bxM/q3s7AiBKNTqEFSnc7Ie+4vAUOcj8NCOyD+Boe//RlEh4Lp05qAB2AHoyjFTYty22IOo44FIe6YQWcDIThU070ivBOlejUutSAAABgu9Xt9AAAAQDAEcwRQIhAJI0kKDx7Ss5KMSddLBCddYLpk0+PDD+CX/S3NCA2OaWAiBZwkiQGZkSCWOkkfC2I0G5TdZV/2mzID9Gh0zA2CikMDANBgkqhkiG9w0BAQsFAAOCAQEAMHrB7SpMLepcQQH0esVfTh6IMJJTtfyhTpbLFph6xOObkCXCYnntYDvCF7jz19IYeD8j295StssjnFhTHK946lr28wtMdtYB3Pmk7xIRjfHZwT8XfLTMO+Zw31k2++ET3JD9UJgLL02v3fXoLQTzvXQ7VNjqR1ygoRsvsymlf5dzgimOKO6X1IcRHQe5mgjqiNMFSmEWeEsJ4kedE4LK7URey1gu4xfXgzlSbo3ADZcB49E2+18ejrh5WTcIrxTRBIFw1wY0y4rKrLrMx8hnqTcDSLIO4vrB0UDE7IkMUDek3qQEpjsaT5Cd8NEx1YODDiuu+ycpF71uuLhwDaniUw==</X509Certificate>
</X509Data>
</KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
</md:KeyDescriptor>
<md:ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x.kenexa.com:9444/sps/inboundSSOProd/saml20/soap" index="0" isDefault="true"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x.kenexa.com:9444/sps/inboundSSOProd/saml20/soap"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x.kenexa.com:9444/sps/inboundSSOProd/saml20/soap"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/login" index="0" isDefault="true"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x.kenexa.com/sps/inboundSSOProd/saml20/login" index="1"/>
</md:SPSSODescriptor>
<md:Organization>
<md:OrganizationName xml:lang="en">Infinite BrassRing Platform</md:OrganizationName>
<md:OrganizationDisplayName xml:lang="en">Infinite BrassRing Platform</md:OrganizationDisplayName>
<md:OrganizationURL xml:lang="en">talentsuite.infinite.com</md:OrganizationURL>
</md:Organization>
</md:EntityDescriptor>
SSO Metadata - EU Production
Abstract
At this present time, the valid SSO Metadata - for EU Production is listed in this document. As noted in the Frequently Asked Questions section of this guide, SSO Metadata certificates for each Infinite BrassRing Platform environment do expire and do need to be replaced on the date and time of expiration. Infinite BrassRing Platform's existing SSO metadata certificate must not be removed before the certificate expires. You will be notified prior the expiration date when to replace your EU Production certificate.
SSO Metadata - EU Production
This Prod-EU metadata certificate is the NEW metadata certificate. Use this certificate for your EU Production environment.
<?xml version="1.0" encoding="UTF-8"?><md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20">
<md:SPSSODescriptor AuthnRequestsSigned="true" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGujCCBaKgAwIBAgIJAK5MyG8QSaPyMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MTgyOFoXDTIzMDgzMDE1MTgyOFowJTEjMCEGA1UEAxMaaWJzc29zaWduLnN0YWdlLmtlbmV4YS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDQ5tv1LSAVMHA/YjveGjqXCl8sJ4OjmMjcffnYzUii3Oq1ItwF+9cT9690itU/drfLK7o7Rr0Hjw26lACsR94eMHTCgU6+38wN/4a/tsw8kMaBBuInHgB0BCHiZ0xGBZkZx/JH/e5AYU9uZC738Pmubx9mezczgX7ixCv0e8/qBdJ4xVT/DKbZJaytzEqimTzU4YfGNxDV/bXfVkrq655r2n6WUEhK3Q7JftbXg63Ag+inTQOUs6zXtt3ec0/GausGypN/dm5zh7SRJ8aTHLYrg3nEd9YX7N9kCVGG81nSwpKcEerc/LbQ2+5eIynS3IVVfHfyNE27p487FwVRIGBDAgMBAAGjggNbMIIDVzAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAOBgNVHQ8BAf8EBAMCBaAwOAYDVR0fBDEwLzAtoCugKYYnaHR0cDovL2NybC5nb2RhZGR5LmNvbS9nZGlnMnMxLTQ0MjQuY3JsMF0GA1UdIARWMFQwSAYLYIZIAYb9bQEHFwEwOTA3BggrBgEFBQcCARYraHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzAIBgZngQwBAgEwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5nb2RhZGR5LmNvbS8wQAYIKwYBBQUHMAKGNGh0dHA6Ly9jZXJ0aWZpY2F0ZXMuZ29kYWRkeS5jb20vcmVwb3NpdG9yeS9nZGlnMi5jcnQwHwYDVR0jBBgwFoAUQMK9J47MNIMwojPX+2yz8LQsgM4wRQYDVR0RBD4wPIIaaWJzc29zaWduLnN0YWdlLmtlbmV4YS5jb22CHnd3dy5pYnNzb3NpZ24uc3RhZ2Uua2VuZXhhLmNvbTAdBgNVHQ4EFgQUVVUnxVgtih97mQZIPQ8w7FkflQcwggF+BgorBgEEAdZ5AgQCBIIBbgSCAWoBaAB2AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9VHUMAAAQDAEcwRQIgO1aTDG1hmCfufQmJ5yjHbe4FJZ2SL+NC0sxoVDnxHWoCIQC3CQXuN257eYMZiSyAOnyBBn3Lg4BDwNpjclDCWvrIRwB3ADXPGRu/sWxXvw+tTG1Cy7u2JyAmUeo/4SrvqAPDO9ZMAAABgu9VHqkAAAQDAEgwRgIhAKTBMG8pfizulvTrI1GKkZP5y2xuQjapBQGeVqysD73iAiEAmp/8vm3oSUjC3FGtaohsEkCUXUlG9zJoaEWcSlAhRdkAdQB6MoxU2LcttiDqOOBSHumEFnAyE4VNO9IrwTpXo1LrUgAAAYLvVR8aAAAEAwBGMEQCIGlwb/Of1e/ouJzv8rlkOZmmp6o5qpnFJ8ERtJU37fG9AiB2CwrcIt0eQTPBREeK5CuOpvYA4EE5+z6JquX1/Se7MTANBgkqhkiG9w0BAQsFAAOCAQEAIEioFruyw9Ve21jvLh/vrIICDqLNKBlDive9CtvLSQJIcDYn9xhsq1+OVUBed1M4TULsYDx4Qnuv+gfjpsH2rLzK0y6jDVJPYhqXnnc28wtDdqdLYTkszxGTAY63d04zmyzuJCJ9gcs7KpVIOfN/E9280ZARgJl5e49drLF5m+TqQxRabb+l0pW8tmHJ2BAFKBVD7EVetH/FEcOstvLDod97U/0SZptMUbGAY1N6LiqWIJI4iNSc1fffn5xaPYloo1cAGdRXvJU36P4fFb3GctQ3x41gID95Aiut2AhTrXwDvLRf6OsyukPIM1BNZ7Scs0Zk0dHf/njzdArYe40Vrg==</X509Certificate>
</X509Data>
</KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGxDCCBaygAwIBAgIJAJ4yar8MbKMwMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYDVQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEaMBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2VjdXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTIyMDgzMDE1MjAwOFoXDTIzMDgzMDE1MjAwOFowKDEmMCQGA1UEAxMdaWJzc29lbmNyeXB0LnN0YWdlLmtlbmV4YS5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCYfMatFNuSY03qlImIc9UFtSuvQowka6cIbGH/TnRkSy4CBYbQEOtfthQp1Wu4uo4Za7aD7vUpKjxtXbEd6irvptAtY0NMBwOkJZfQtymDFZ9zJq7U5aHnBD//m3FZCGg/5z+XdAxVfKMBk0WTzaVPm2/8pjgbLvKOgpr5iHIfg72Ywwz98fjz+LN2qlsg0tlv/jKaM6g8WQEFqjzao7vZweT/BNWwI6ORh45cGCTEKCg/0Mq2DlUZGXAfHfo/ddgNieqC6Izi+44gg9fx0UpMVr8PO5DFjm3iJCgJvtqnvSJhGyf0lbExoL/s27cEqoEqmIaFYaayaMCwWHqqc6qHAgMBAAGjggNiMIIDXjAMBgNVHRMBAf8EAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjAOBgNVHQ8BAf8EBAMCBaAwOAYDVR0fBDEwLzAtoCugKYYnaHR0cDovL2NybC5nb2RhZGR5LmNvbS9nZGlnMnMxLTQ0MjQuY3JsMF0GA1UdIARWMFQwSAYLYIZIAYb9bQEHFwEwOTA3BggrBgEFBQcCARYraHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzAIBgZngQwBAgEwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5nb2RhZGR5LmNvbS8wQAYIKwYBBQUHMAKGNGh0dHA6Ly9jZXJ0aWZpY2F0ZXMuZ29kYWRkeS5jb20vcmVwb3NpdG9yeS9nZGlnMi5jcnQwHwYDVR0jBBgwFoAUQMK9J47MNIMwojPX+2yz8LQsgM4wSwYDVR0RBEQwQoIdaWJzc29lbmNyeXB0LnN0YWdlLmtlbmV4YS5jb22CIXd3dy5pYnNzb2VuY3J5cHQuc3RhZ2Uua2VuZXhhLmNvbTAdBgNVHQ4EFgQU2/6qp8LpqJD5aEIPUFmZtoNgCg8wggF/BgorBgEEAdZ5AgQCBIIBbwSCAWsBaQB3AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nhd31tBr1uAAABgu9Wp2IAAAQDAEgwRgIhAI++D8ZOGmhaH/tVhLIR8k9EnNcxRhKaMV2QvMu3sJ22AiEA96W2+k+kAg0RxAl3VSXs6mYqEVOzcLuUE9ANCXvVFYsAdgA1zxkbv7FsV78PrUxtQsu7ticgJlHqP+Eq76gDwzvWTAAAAYLvVqi1AAAEAwBHMEUCIQC8bNf5sWlZGN68tTWYe1yKmHs7kQWLcfZ+2qwEPO3eMQIgQNGQTAN23wLnd7l+R9RwXBjz2jNoSfNBmnFuj/8Hvi0AdgB6MoxU2LcttiDqOOBSHumEFnAyE4VNO9IrwTpXo1LrUgAAAYLvVqkxAAAEAwBHMEUCIF82mX7c2tp/o8o2fEkAe6+CyHmtgwP6DazHlyF2tXBUAiEA+H4iylGfr0qjovycWmao6isexO+vq794HbIuruJJsYYwDQYJKoZIhvcNAQELBQADggEBAEDKaOdFz0DNNKUAMmy5ZYfr+T3qQDtPex6LdeNCzykNox0QXmg6LsnKu0QpsdxK0kN1SB40OqqWd+1TkagXiESsYocOILuspoKHyNit7Drfu3DKZHYOUqIfycn43ijipEU5g1d1fLipODRoHg5JY/XrYBouRBQ7Lh3WrTs07OKagUc6Cv2YSQC0+JQ4pL8mxpDNszYuCTsGjkzEvVJfy+MpKgK0FM0VprJncxghWtl19FNAVotKi7lztn+6Uae24Y0OXrfSM2PNtcujS2z1A/W6LC3zKETIPyVmEOdnLIyRPGPJVCGnYXRdZt942syrcPvAeQ7yxr/22+thNOrN/5s=</X509Certificate>
</X509Data>
</KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5"/>
</md:KeyDescriptor>
<md:ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap" index="0" isDefault="true"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/slo"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/mnids"/>
<md:ManageNameIDService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://2x-staging.kenexa.com:9444/sps/inboundSSOStage/saml20/soap"/>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://2x-staging.kenexa.com/sps/inboundSSOStage/saml20/login" index="1"/>
</md:SPSSODescriptor>
<md:Organization>
<md:OrganizationName xml:lang="en">Infinite BrassRing Platform - Stage</md:OrganizationName>
<md:OrganizationDisplayName xml:lang="en">Infinite BrassRing Platform - Stage</md:OrganizationDisplayName>
<md:OrganizationURL xml:lang="en">talentsuite.infinite.com</md:OrganizationURL>
</md:Organization>
</md:EntityDescriptor>
How to Configure Inbound SSO
Abstract
Infinite BrassRing Platform Administrators with the role of SSO Administrator configure Inbound SSO and manage certificates. Configuring Inbound SSO requires the exchange of XML metadata and security certificates.
Configuring Inbound SSO
Infinite BrassRing Platform Administrator logs in to Infinite BrassRing Platform:
Selects the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Selects the Admin action on the Infinite BrassRing Platform navigation bar. The Administration application opens.
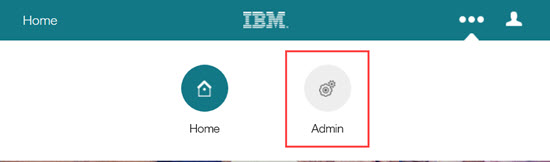
Opens hamburger menu and selects SSO → Inbound.
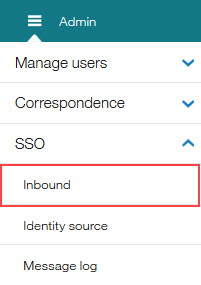
The Edit Inbound SSO configuration page opens.
Note
Only a portion of the page is shown in this screen capture.
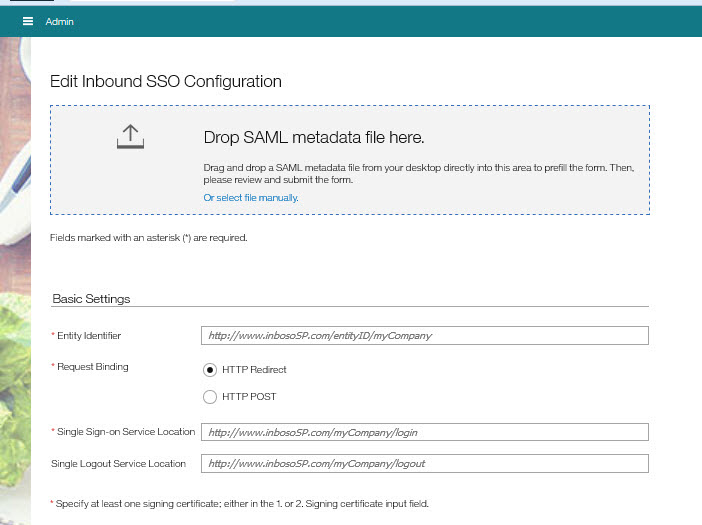
Selects their SAML Metadata file and drops it into the Drop SAML metadata file here container. Alternatively, user can Select file manually. When the metadata file is accepted, the Inbound SSO fields, Entity Identifier, Request Binding, Single Sign-on Service Location, Single Logout Service Location auto-populate.
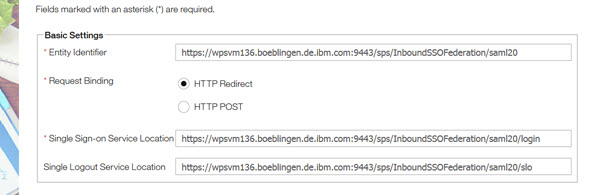
User accepts the HTTP Redirect or selects the HTTP POST designation.
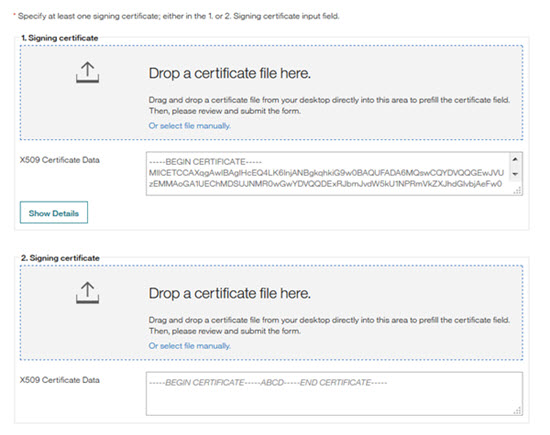
Scrolls to the Signing Certificate section, selects their Security Certificate file and drops it into the Drop a certificate file here container. Alternately, user can Select file manually. The Certificate Data field auto-populates. User can select Show Details to view the certificate details.
Note
Configuring two security certificates to ensures that when one certificate expires, the secondary certificate can be immediately selected to replace the expired certificate. Installing two certificates ensures a minor interruption of service. Users have 14 days from the Security Certificate expiration date to update their security certificates.
Scrolls to the Encryption Certificates, selects their Encryption Certificate file and drops it into the Drop a certificate file here container. If the encryption certificate data is contained in the metadata file, this field auto-populates. Alternately, user can Select file manually. The Certificate Data field auto-populates.
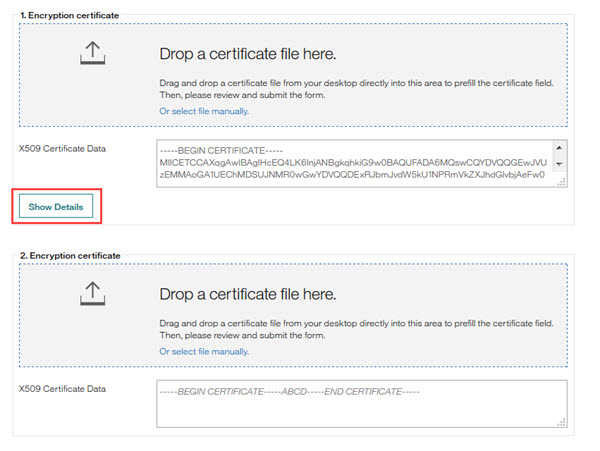
User can select Show Details to view the certificate details.
Scrolls to the Advanced Settings section.
Selects the check box for Consider all users eligible for SSO.
Note
There are two required steps to assign all users to be Eligible for SSO. Administrators must select the check box for Consider all users eligible for SSO AND enable the Infinite BrassRing Platform users for SSO when Infinite BrassRing Platform users are added to or edited in the Infinite BrassRing Platform. Consider all users eligible for SSO is an alternative option that is used during user imports. Administrators need to remember to disable this feature, Consider all users eligible for SSO so that only SSO enabled users can access the system through the client's SSO in the future. Depending on the number of users being imported, importing might take a long time to complete. Alternatively, Administrators can import users and enable the Consider all users eligible for SSO option during import. Using this option is a two-step process. First, users are imported with the setting Consider all users eligible for SSO and after import, users need to be added as Infinite BrassRing Platform users AND be enabled for SSO.
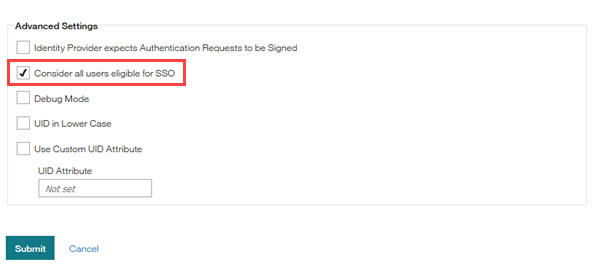
Note
The Consider all users eligible for SSO is intended only to be used temporarily.
Selects Submit.
Setting up the Relationship with ADFS
Abstract
Managing Active Directory Federation Service ADFS is a standards-based service that provides a way for companies (also known as federations) to securely share identity information. ADFS does not authenticate users itself but facilitates the communication between the companies and can be configured by using claims. Partner companies define and exchange these claims and then map them in the ADFS trust policy. When users access Infinite BrassRing Platform, ADFS checks the claims to determine whether the user is identified in the trust policy, and if so, passes the user onto the SSO authentication.
Configuring and Managing Active Directory Federation Service (ADFS)
Setting Up an ADFS Workflow
To support an SP initiated SAML 2.0 communication, Infinite BrassRing Platform Administrators must add two custom claims to the ADFS configuration.
Open your ADFS take the following actions to add your two claims.
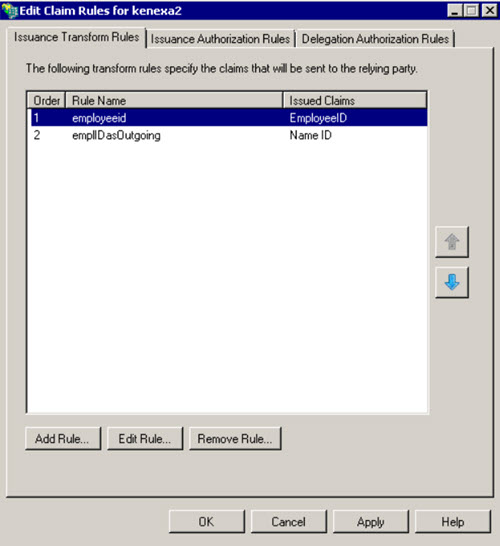
Claim One.
In the following instructions, the employeeID and NameID values were used.
Browse to Relying Party Trusts → Name of Relying Party Trust → Edit Claim Rules.
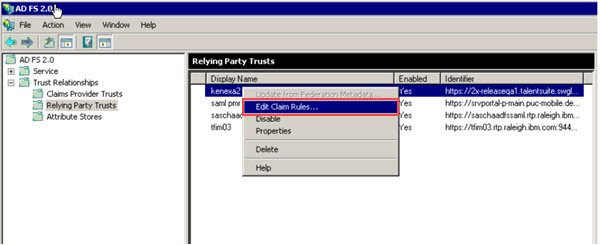
Select Edit Claim Rules.
Select Add Rule.
Select the Send LDAP Attribute as Claims template. The Claim Rule dialog opens.
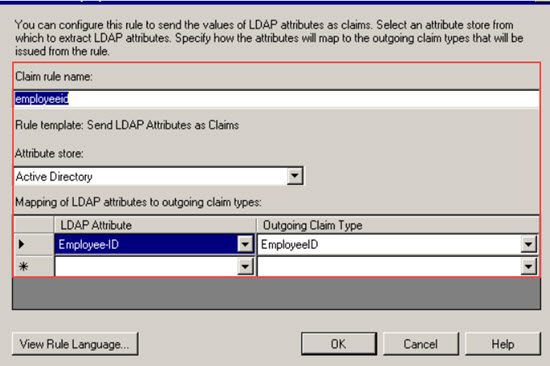
Name the claim rule employeeID.
Select Active Directory as the attribute store.
Select EmployeeID as the LDAP attribute.
Note
The EmployeeID is a custom created claim type definition. Administrators can chose to enter a freetext name.
Select View Rule Language to view the rule language:
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"] => issue(store = "Active Directory", types = ("http://temp.org/employeeID"), query = ";employeeID;{0}", param = c.Value);
Select OK to save the claim.
Claim Two.
In the following instructions, the employeeID and NameID values were used.
Browse to Relying Party Trusts → Name of Relying Party Trust → Edit Claim Rules.

Select Edit Claim Rules.
Select Add Rule.
Select the Transform an incoming claim rule template. The Edit Rule - empIDOutgoing dialog opens.
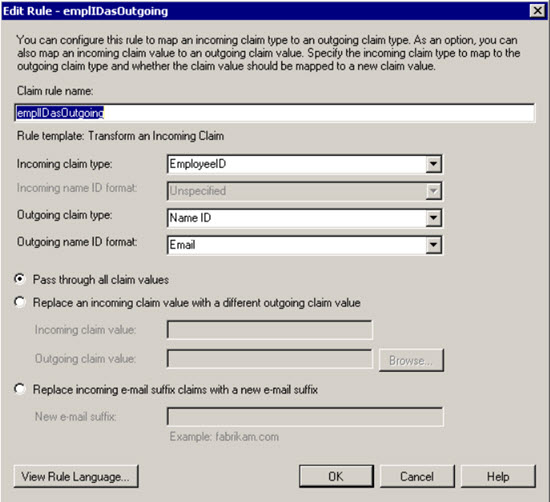
Click on Add Rule and Choose a “Send LDAP Attribute as Claims” Rule Template Select Active Directory as Attribute Store Map the LDAP attribute Employee-ID to the Outgoing Claim Type EmployeeID Note: We have created a custom Claim Type Definition for EmployeeID. This is not required. You can use a freetext name as Outgoing Claim Type. If you do so remember the correct typing as you need it in the second step
Name the claim rule employeeIDasOutgoing.
Select EmloyeeID for the Incoming Claim Type.
Select NameID for the Outgoing Claim Type.
Select Email as the Outgoing Name ID Format.
Select the radio button for Pass through all claim values.
Note
The EmployeeID is a custom created claim type definition. Administrators can chose to enter a freetext name.
Select View Rule Language to view the rule language:
c:[Type == "http://temp.org/employeeID"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");
Select OK to save the claim.
This configuration results within this Claims Rules chain. If you login now to this instance using IdP or SP initiated, the login submits the EmployeeID as the NameId field.
<Subject> <NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">007</NameID> <SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"> <SubjectConfirmationData NotOnOrAfter="2016-03-23T15:07:49.936Z" https://2x-releaseqa1.talentsuite.swglab.ibm.com/sps/inboundSSOiQA/saml20/login /> </SubjectConfirmation> </Subject>
Note
For Troubleshooting ADFS-specific issues, see SAML - ADFS Specific in the troubleshooting section of this guide.
Federating the Infinite Talent with Configuration Data of Customer Identity Provider (IdP)
Abstract
Configuring Single Sign-On (SSO) for the Infinite BrassRing Platform requires the configuration of Inbound SSO. Inbound SSO requires the exchange of security certificates that establish authentication trust between the customer system and .
Federating the Infinite Talent with Configuration Data of Customer IDP
Configuring Single Sign-On (SSO) for the Infinite BrassRing Platform requires the configuration of Inbound SSO. Inbound SSO requires the exchange of security certificates that establish authentication trust between the customer system and Infinite BrassRing Platform.
Federating the Customer Environment with Configuration Data of Infinite Talent SP
Note
Only Infinite BrassRing Platform Administrators with the role of SSO Administrator are allowed to configure Inbound SSO and to manage certificates.
Inbound SSO
To configure Inbound SSO, Administrators log in to the Infinite BrassRing Platform Application and provide configuration data, SAML metadata, and security certificates to establish SSO. The following sections outline the required data types necessary to successfully establish SSO.
SAML Metadata
The following SAML metadata can be set with an inbound SSO configuration:
Entity Identifier (mandatory)
Request Binding (must be either HTTP POST or HTTP Redirect: applies to both single sign-on and logout service location)
Shorter SAML protocol messages can be carried with HTTP GET requests, thus, HTTP Redirect can be used as request binding in this case. HTTP POST allows for longer SAML protocol messages like encrypted and signed messages.
Single sign-on service location (limited to exactly one location)
Single sign-on service location (limited to exactly one location) Signing certificate (at least one, not more than two certificates)
When the IDP is asked to authenticate a user, the IdP signs the authentication response with the signing certificate to allow the receiving SP to validate the response.
Encryption certificate (up to two certificates)
To ensure that the authentication response that is sent by the IdP to the SP cannot be read by other parties, an encryption certificate can be used.
General information on metadata
Additional Configuration Data
The following additional configuration data can be set with an inbound SSO configuration:
Indicator if Identity provider expects authentication request to be signed.
You can check this feature in case you want to have your identity provider expect all authentication requests to be signed requests. This feature is not enabled by default.
Indicator if users are considered eligible for SSO.
In order to ease migration to SSO, this feature disregards the user-specific SSO-setting (considering all users eligible for SSO). It is enabled by default and gives Administrators time to migrate the SSO-setting of all users. After migration of the SSO-setting of all users, Administrators can disable this feature.
Indicator if UID is expected in lowercase.
You can check this feature if the user name in the incoming SAML request is not lowercase, but the user name is lowercase in GateKeeper, respectively the Infinite BrassRing Platform. This feature is not enabled by default.
Indicator if custom UID property is to be used.
You can specify a custom UID property if the user name is not being passed in the NameID field of the incoming SAML request. With this custom UID property, you can specify the property name that is being used instead.
In order to specify a custom UID property, you first must check the box 'use custom UID property'. The custom UID property is not used by default.
Custom UID property
Configuring Identity Source
Abstract
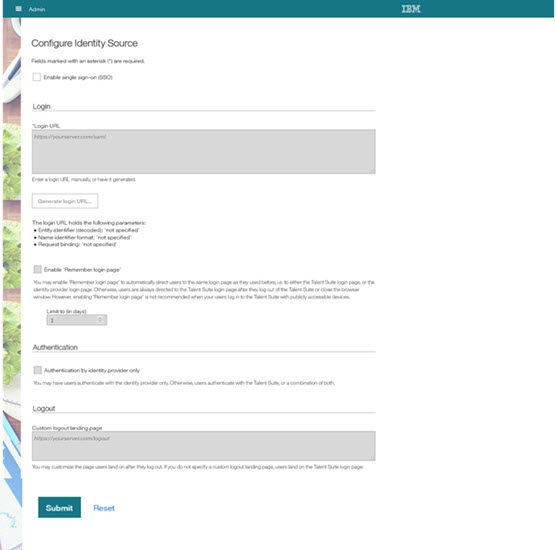
Configuring the Identity Source requires the configuration of the Login URL. Optional configurations include configuring a Remember login page option, an authentication option, and configuring a custom Logout landing URL.
Note
Configuring the login URL requires information on the following configuration data:
Name identifier format
When the SP and IdP communicate, the name identifier format is used to identify the subject. Using the same identifier format allows the SP and IdP to communicate.
Entity identifier (only used when Administrators configure the login URL manually)
Request binding (only used when Administrators configure the login URL manually
You can find this information in these configuration data in the SAML metadata file that is exported from the customer IDP. Make sure to choose the correct instances of the name identifier format, entity identifier, and request binding, since there might be multiple occurrences in the SAML metadata file.
Navigating to the Identify Source Configuration
Infinite BrassRing Platform Administrator logs in to Infinite BrassRing Platform:
Selects the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Selects the Admin action on the Infinite BrassRing Platform navigation bar. The Administration page opens.

Browses to the Admin.
Opens the hamburger menu and on the in-app navigation menu selects SSO Identity Source.
The Configure Identity Source page opens.
Enabling SSO
On the Configure Identity Source page Admin:
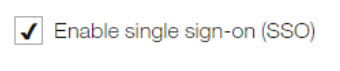
Selects Enable SSO .
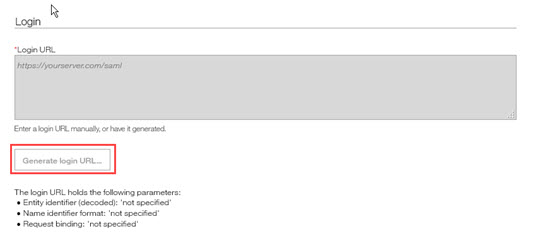
Configuring Login URL
On the Configure Identity Source page the Administrator:
Selects the Generate Login URL wizard to open the name identifier format.
Note
The wizard can be used only after you complete the inbound SSO configuration. See Federating the Infinite Talent with Configuration Data of Customer Identity Provider (IdP) .
Selecting the Generate Login URL opens a dialog box where the administrator selects the name identifier format from the options provided. The options that are selected are set with the SAML assertions.
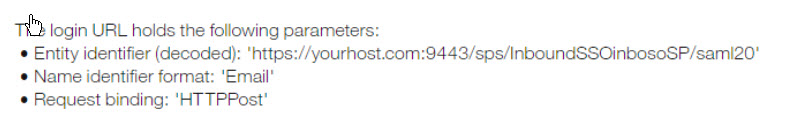
Selects OK. The wizard overwrites any URL already configured in the 'login URL' form field. However, administrator can also input a URL manually although it is not recommended. Users select this generated link to be directed to the client's SSO authentication site.
Note
The identity source configuration form extracts particular URL parameters from the login URL entered and displays them for easy verification.
Configuring Remember login page (optional)
The Administrator next selects Remember login page to automatically direct users to the same login page as they used before. For example, users can be directed to either the Infinite Talent login page, or the IDP login page. Administrators can limit the Remember login page page functions to a number of days in the Limit to (in days)form field. If you do not select Remember login page, users are always directed to the Infinite Talent login page after they log out of the Infinite Talent or close the browser window.
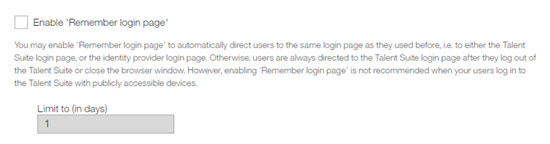
Note
Enabling Remember login page is not recommended when your users log in to Infinite Talent with publicly accessible devices.
Configuring Authentication (optional)
On the Configure Identity Source page the Administrator:
Selects Authentication by identify provider only so that users authenticate only with the IDP.
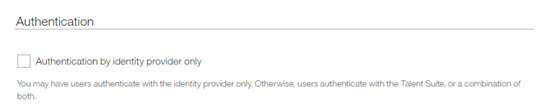
If Administrators do not enable Authentication by identify provider only, users authenticate with Infinite Talent, or a combination of both.
Configuring Logout (optional)
On the Configure Identity Source page:
Administrators can input a custom logout landing page to customize the page users land on after they log out of Infinite Talent.
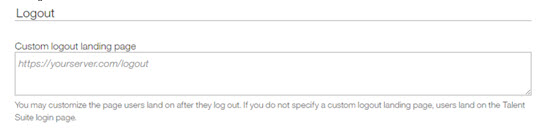
If you do not specify a custom logout landing page, users land on Infinite Talent login page.
Verifying the SSO Configurations
Abstract
Verifying your SSO configurations ensures that SSO is set up properly.
Verifying the SSO Setup
Verifying the SSO configuration is a multi-step process and includes the following tasks:
Enabling an Administrative user for SSO.
Browsing and checking the message log for successful synchronization of the Inbound SSO configuration.
Logging in as the SSO enabled Administrative user.
Enabling an Administrative User with SSO
To enable an administrative user, follow the procedure that is outlined in Enabling SSO for a Single User the for a dedicated Administrative user.
Navigating to the Message Log
Use these steps to browse to the message log:
Log in to the Infinite Talent as an SSO Administrator.
Select the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Selects the Admin action on the Infinite BrassRing Platform navigation bar. The Administration application opens.

Opens the hamburger menu and selects SSO → Message Log.
The Message Log page opens.
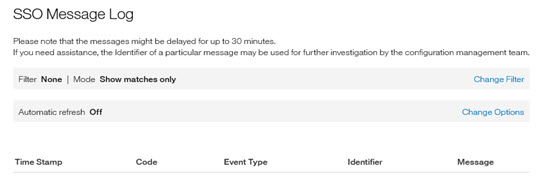
Checking For Successful Synchronization of the Inbound SSO Configuration
On the Message Log page, the following message in the message log indicates a successful synchronization:
HIWAA0202I (configuration created in SP)
HIWAA0201I (configuration updated in SP)
Note
This message indicates that any changes to the inbound SSO configuration are being synchronized to the IDP in Infinite Talent. However, the synchronization process takes at least 20 minutes to complete. Thus, you must wait for the synchronization to successfully complete before you can initiated tests on the updated configuration.
Logging in With SSO Enabled Admin User
The last step in the verification process is to log in as an SSO Enabled Administrative User.
Note
Before you initiate any tests that are related to an updated inbound SSO configuration, make sure that the inbound SSO configuration is successfully synchronized. See the previous step, Checking for Successful Synchronization of the Inbound SSO Configuration. And, use an Admin user that is enabled for SSO. See Enabling an Admin User for Use with SSO.
Log in to the Infinite Talent as an SSO Administrator.
Note
If an Administrator enabled the Authentication by identity provider only option that is described in Enabling SSO for a Single User, you are redirected to the login page of the customer IDP to enter your credentials. If this option is not enabled, use the Existing Employee? Log in here. link on the login page of Infinite Talent.