Abstract
This page describes Single Sign-On (SSO) Error Messages that might be encountered when configuring Infinite BrassRing Platform SSO.
When SSO configurations are unable to complete successfully, error messages generate and provide specific information to resolve those errors. The error messages on this page are the most commonly encountered during SSO configuration. Generally, error messages generate a code identifier.
For more information on troubleshooting ADFS, Azue, and Okta issues, refer to Azure AD, Okta, and ADFS Troubleshooting
Failed to save Inbound SSO configuration
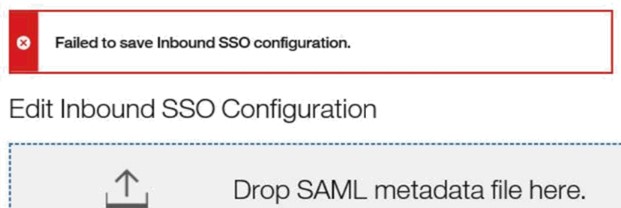
Description: This error can display after selecting Submit on the Inbound SSO page when a required field is left blank.
Solution: When a metadata file is uploaded, in rare cases, the certificate, or other information might not be parsed as expected. This can result in some required fields not populating. Verify that the required fields have values and the signing certificate is correct by selecting Show Details before selecting Submit.
If the certificates are available in the metadata but not being populated, manually extract the certificates from the metadata file and paste the certificate data into the [X509 Certificate Data] section. Alternatively, save the certificates to a file and upload it to the certificate section.
HIWAA0002W
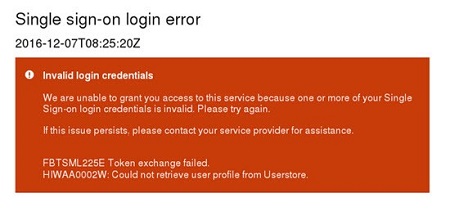
Description: SAML message and general communication are working as expected although there is an invalid user error. The User Id provided inside of the SAML assertion does not match to any users within the Infinite BrassRing Platform.
Solution:
Verify that the IdP's SAML Response includes the username in the [NameID] field. Refer to the How to Obtain SSO SAML Communication Traces topic in the Debugging SSO Issues section for guidance on how to obtain SSO SAML Response.
Verify that this user is provisioned, and active in Infinite BrassRing Platform User Management. If not, refer to How to Add New User.
Usernames are case sensitive. Verify that the case of the username sent by the IdP matches the case of the username in Infinite BrassRing Platform. (For example: If the IdP's SAML Response is [Bsmith], and the Infinite BrassRing Platform username is [bsmith], then this error displays.)
If all Infinite BrassRing Platform user names are in lower case, select UID in Lower Case when configuring the Infinite BrassRing Platform Service Provider. (For more information, refer to Configure Talent Suite Service Provider (SP) Inbound SSO.) This automatically converts all IdP provided usernames in the [NameId] field to lower case.
If the case does not match, update the username in either Infinite BrassRing Platform or the IdP system to match the case used.
FBTSTS019E
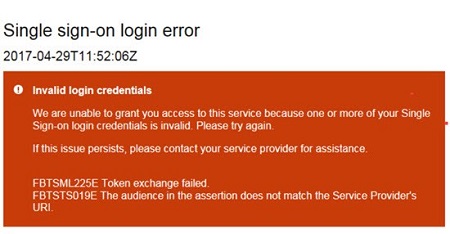
Description: The received assertion includes a targeted audience that does not match the Identifier of the server.
Solution: Search for the Audience element within the SAML Response. For more information, refer to How to Obtain SSO SAML Communication Traces on the Debugging SSO Issues page. The correct audience for the staging environment is: https://stagingts.brassring.com/sps/inboundSSOStage/saml20, and the correct audience for the production environment is: https://ts.brassring.com/sps/inboundSSOProd/saml20. Verify with the client and then change the Audience field to match the server EntitylD.
FBTSML210E
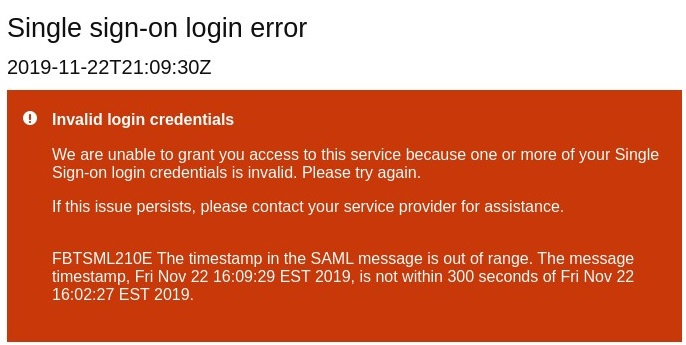
Description: Infinite BrassRing Platform SSO is configured to allow 300 seconds for the SSO protocol to be completed. This gives the user time to enter their login credentials into the IdP system, and addresses any potential time drifts between the Infinite BrassRing Platform and IdP clocks. (This issue could be caused by an incorrectly configured clock on the IdP system, or if the issue is only for one user, a slow connection, or system, might mean that Infinite BrassRing Platform is not receiving the SAML response within the 300-second window.)
Solution: If the issue is system wide, the IdP administrator should review the clock settings on the IdP server. If the issue only occurring for one user, review the user's system, or network connection, to verify it can receive the response within the 300-second window.
FBTSML225E / FBTSTS001E
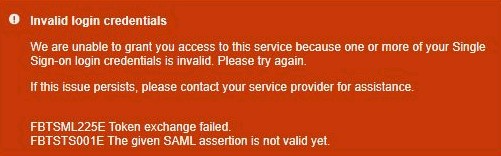
Description: This usually happens when the given SAML assertion's [NotBefore] time has not been reached during the SSO handshake.
Solution: Ensure that the IdP server's clock is synchronized. For ADFS based IdP systems, refer to SAML Clock Handling ADFS on the Azure AD, Okta, and ADFS Troubleshooting page.
FBTSML236E
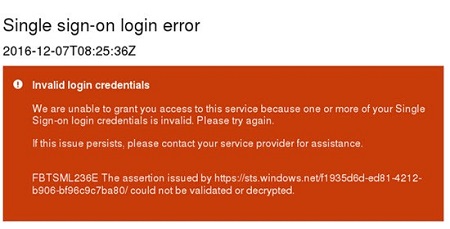
Description: The received assertion might not be validated. Generally, this message means that either an incorrect certificate is stored inside of the configuration or the validity of the token has timed out.
Solution: If encryption is being used, disable the encryption to verify whether the issue is caused by the encryption. The use of encryption is optional. For more information on disabling encryption in an ADFS-based IdP, refer to the Temporarily Disable Encryption section in Azure AD, Okta, and ADFS Troubleshooting, or review the ADFS documentation.
To check the validity of the IdP’s certificate, refer to How to check the validity dates of an IdP certificate? in the Frequently Asked Questions section.
Note
After any encryption or certificates are updated to resolve this issue, it can take 5 minutes in the Staging environment or 15 minutes in the Production environment to sync the changes. The error might still appear if testing is done before these time periods elapse.
FBTSML241E
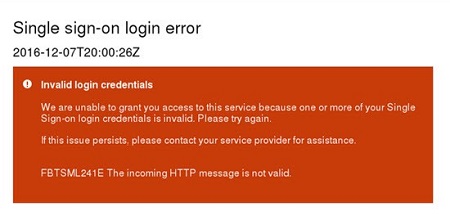
Description: The processed request on the SAML endpoint is not valid. This error type might be caused by missing or incorrect parameters or values in SAML AuthnRequest or SAML Response.
Solution: This issue usually happens in the IdP initiated flows. Make sure that SAML Response is properly formatted, especially the value of the RelayState in the SAML is correctly defined or mapped to Infinite BrassRing Platform's entityID. Contact your organizations IdP administrator for further assistance on checking the IdP event logs.
FBTSML224E
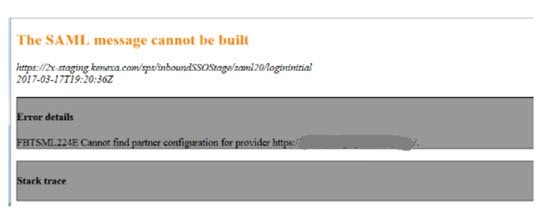
Description: The SAML error message is that the SAML message cannot be built. This error can be caused by an incorrect configuration within the Inbound Page and the Identify Source page. Verify that the Entity Identifier and the Unique Name values match.
Solution: The SAML status included in the authentication response message indicates that authentication failed at the identity provider. Examine the trace logs on the identity provider that issued the response message to see why the authentication operation failed.
FBTSML242E
Inspect and verify that the username in the NameID field in IdP's SAML Response matches to username defined in Infinite BrassRing Platform User Management. (The username is case-sensitive.)
If the usernames do not match, either update the username in Infinite BrassRing Platform User Management to match to what is sent in SAML Response, or work with your organizations IdP administrator to send the matching username in the NameId field.
If the usernames match, refer to Tivoli Federated Identity Manager related error messages: FBTSML242E .
Other Error Messages
For information on other error messages that might be encountered, refer to Single sign-on protocol service messages