The following diagram summarizes the SP-initiated SSO process.
Standard SP-initiated SSO process
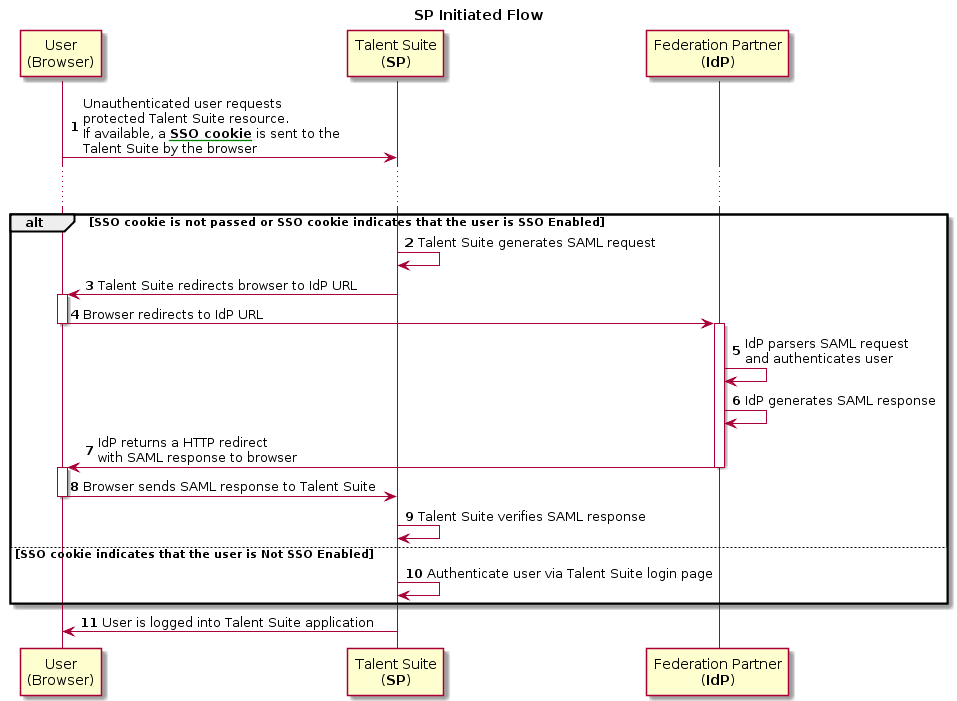
As shown in the diagram, the SP-initiated process steps are:
User, who is currently not logged onto the Infinite BrassRing Platform site, attempts to access a protected Infinite BrassRing Platform resource. If available, then a SSO cookie is submitted along with the request to the Infinite BrassRing Platform login page. SSO cookie is available if, for example, a user has already logged on to the Infinite BrassRing Platform using this browser.
The SSO cookie submission results in one of three possible scenarios.
Scenario 1: SSO cookie does not exist. If this is the case, then Step 2 is:
Refer to the Enhanced User Experience SP-Initiated SSO section of this document.
Scenario 2: SSO cookie exists, and indicates that the last browser user was SSO enabled. If this is the case, then Steps 2 through 11 are:Federation server generates a SAML request.
Federation server returns HTML form to browser, with the IdP's SAML request for authentication.
HTML form is automatically posted to IdP's SSO service.
IdP's SSO service:
Parses SAML request.
Authenticates user, either by requesting valid credentials or by checking for valid user session.
IdP federation server generates SAML response containing authenticated user's username. In accordance with SAML 2.0 specification, SAML artifact is digitally signed with customer's public and private certificates.
IdP federation server sends HTTP redirect containing the artifact through the browser to Infinite BrassRing Platform federation server.
Browser automatically posts HTML form back to Infinite BrassRing Platform as per HTTP redirect information.
Infinite BrassRing Platform SSO service verifies SAML response using IdP's public key.
If a valid assertion is received, then a session is established on the Infinite BrassRing Platform and the browser is redirected to the target resource.
Session is established on Infinite BrassRing Platform and browser is redirected to target resource.
Scenario 3: SSO cookie indicates that user is not SSO enabled. If this is the case, then Steps 10 and 11 are:
10. The user is redirected to the Infinite BrassRing Platform login page for authentication.
11. If the user's credentials are valid, then a session is established on the Infinite BrassRing Platform and the browser is redirected to the target resource.Once the user has been authenticated, either by the IdP's SSO service or the Infinite BrassRing Platform login page, a cookie is stored in the user's browser. This cookie will be used to identify the user's SSO status the next time the user tries to access a Infinite BrassRing Platform protected resource via the SP-initiated flow.
Standard SP-Initiated SSO User Experience
Abstract
In the standard SP-Initiated SSO experience, browser cookies enable the Infinite BrassRing Platform to identify an unauthenticated user, and direct that user to the appropriate login page to authenticate.
The cookie is generated and valued with the login method last used to access the Infinite BrassRing Platform. Upon initiation of an SP-initiated workflow, the Infinite BrassRing Platform references this cookie to determine which login page the user should see when authentication is required:
Client users outside the IdP (e.g., external candidates) access the Infinite BrassRing Platform via the Infinite BrassRing Platform login page.
Client users inside the IdP (e.g., employees) access the Infinite BrassRing Platform via their company intranet login page.
If a user is being automatically redirected to the wrong login page, it is advised to clear the browser cookies.