Troubleshooting
Abstract
When SSO configurations do not operate as expected, configuration changes might be required. For example, there could be a failure to establish trust between the client's system and Infinite BrassRing Platform, an incorrect ADFS configuration, or you might encounter SSO error messages. The following sections outline common configuration errors.
Frequently Asked Questions - Setting up SSO
Q: How do I obtain the ACS URL for Infinite Talent?
A: If the ACS (Assertion Consumer Service) URL is required during the SSO configuration in your IdP system such as Azure or Google, this information can be found in each environment's SSO Metadata files as the "Location" attribute value of the md:AssertionConsumerService tag.
Q: Can clients put their new Signing and Encryption Certificates in the Signing Certificate and Encryption Certificate fields?
Figure 103. Signing Certificate field
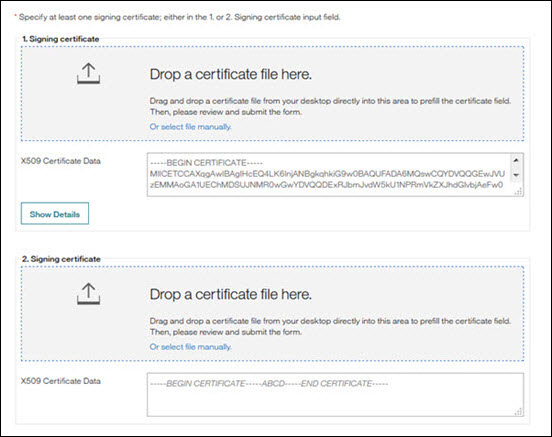
Figure 104. Encryption Certificate field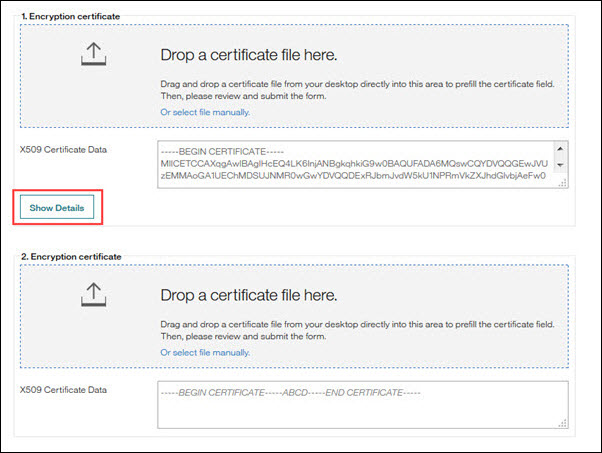
A: Yes. The second field is for the update.
Q: Will the Infinite BrassRing Platform automatically uses the Signing and Encryption Certificates in the second field if the Certificates listed in the first field are expired?
Figure 105. Infinite BrassRing Platform automatically uses the Signing and Encryption Certificates in the second field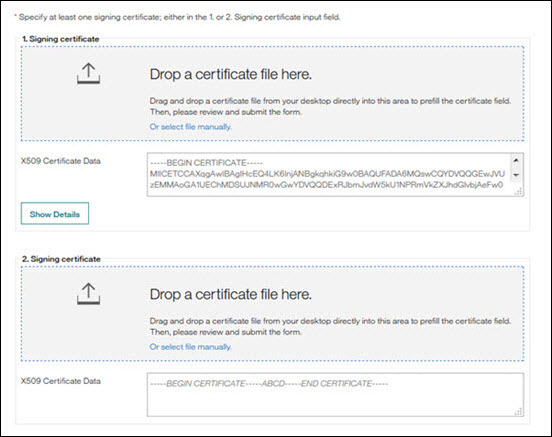
A: Yes, if the Certificate Authority and the issuer DN did not change. If either of them changed, we cannot identify that the two certificates belong together and therefore it would require an admin to schedule a time to go into the UI to place the new Certificate into spot 1 at the time the change needs to happen.
Q: When the Signing and Encryption Certificates in the first field expire, will the Certificates in the second field automatically move up to the first field location such that the second field will be blank and available for next year’s new Certificates?
A: No. There is no automated move, but the certificate in the first field is automatically marked as invalid when it expires. If the admin users come back the next year, they will be able to spot which one to choose.
Q: When the Infinite's Encryption and Signing Certificates for the Infinite BrassRing Platform SSO in Production expires, will the new Infinite BrassRing PlatformMetadata information (Encryption & Signing Certificate information) be available for the Infinite Production Environment in this Knowledge Center.
A: Yes. Before the Infinite Talent Certificate for SSO expires, a communication will be sent to clients using SSO. The communication will have the details on when the new certificate will be activated, how to obtain the new Certificate, when the old one will expire, the steps that might need to be taken by the clients, and what changes might occur in the metadata file, if any.
Q: Is there an annual date that these Certificates expire for Infinite? Or, do these Certificates expire a year from the date the SSO was set up between the client and Infinite?
A: It is an annual, global date.
Q: Once the client has the new metadata from Infinite Talent, the client needs to update their IdP system such as ADFS and resubmit to the IdP team.
A: The client can pass the Certificate by extracting from the metadata file and/or pass the metadata file directly. However, depending on the configuration in the IdP system, the signature change might not even be needed. If they setup their system without a signature validation, their system would continue to work even without them refreshing our Certificate.
Q: If a client is using Ping Identity for their SSO solutions, how can they construct their IdP SSO URL for Talent Suite?
A: The client would need to use PartnerSpId in their URL pattern as indicated in the Ping Identity documentation at this URL location https://docs.pingidentity.com/bundle/pf_sm_publishingMetadata_pf83/page/pf_t_provideSamlMetadataByUrl.html. If they use PartnerId or PartnerIdpId, that will not work. (For example: https://clinet's-idp-url?PartnerSpId=https://ts.brassring.com/sps/inboundSSOProd/saml20&TargetResource=https://ts.brassring.com/wps/myportal/$tenant/client-name.)
Resolving the SSO Certificate Parsing Error
Abstract
Talent Suite does not accept certificate files in binary format and requires that all certificate files be x509 certificates in base64 format. You can ensure that your certificates meet the requirements by opening the .cer file using your certificate tool and exporting the .cer file in base64 format.
SSO Certificate Format Error
When you add, refresh, or replace a certificate in your Inbound
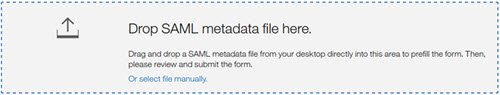
SSO Configuration, and encounter the Error Parsing File error message, it might be because the certificate file is not in the base64 format.
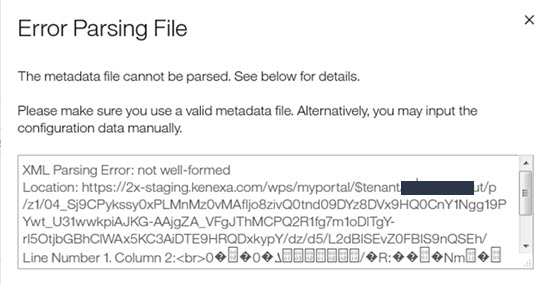
Use the procedure that follows to export the .cer file into the base64 supported format.
Exporting Your Certificate into the base64 Format
Use the following procedure to export your certificate into the base64 supported format.
Browse to your certificate file and open the file.
Select the Details tab and then select Copy to File.
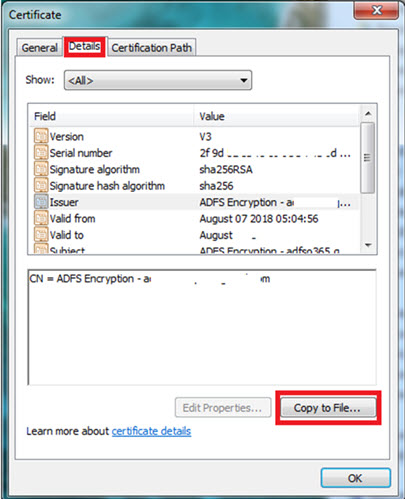
Select Next on the Certificate Export Wizard modal.
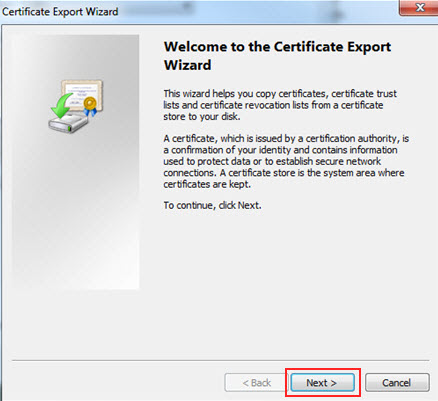
Select the radio button for Base-64 encodd X.508 (.CER).
Select Next.
Browse to your certificate file and specify the certificate file name and location.
Select Next.
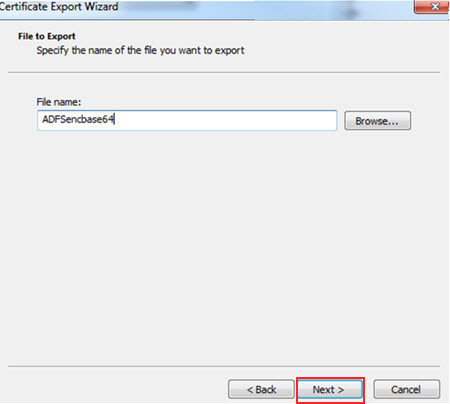
Select Finish to complete the export.
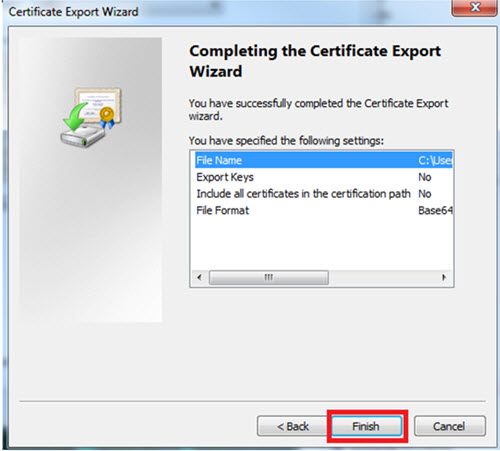
The modal redisplays and indicates the export was successful.
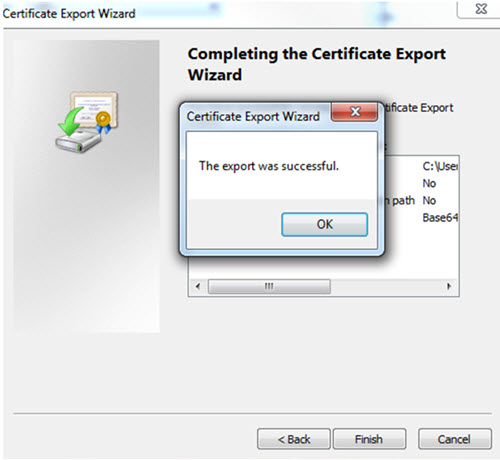
Select OK and Finish. You can now continue to add, refresh, or replace the existing certificate with the exported certificate in the base64 format.
Replacing an Expired Certificate
Abstract
Administrators sometimes need to replace an expired certificate.
Navigating to the Inbound SSO
Infinite BrassRing Platform Administrator logs in to Infinite BrassRing Platform:
Selects the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Selects the Admin action on the Infinite BrassRing Platform navigation bar. The Administration page opens.
Opens hamburger menu and selects SSO → Inbound.
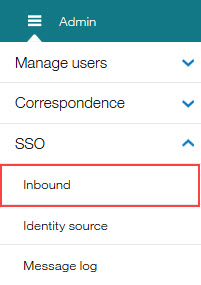
The Edit Inbound SSO Configuration page opens.
Adding a new Certificate
Administrators must find the location of the expired certificate in order to add the new certificate. Administrator:
Locates the This certificate is expired message. The location of this message determines where the Administrator need to place the new certificate. For example, if it is the signing certificate that expired, the new certificate needs to be placed in the slot where the expired certificate is located.
Drops the new certificate into the respective slot. Copy and paste can also be used to place the new certificate.
Selects Submit.
Note
If you encounter a parsing error when you submit the new certificate, see Resolving the SSO Certificate Parsing Error.
SAML - ADFS Specific
SAML Clock Handling ADFS
The SAML clock is an integral part of the SAML and SSO authentication process. Establishing trust between the client's system and the Infinite BrassRing Platform requires the exchange of valid credentials. IdP defines a credential (assertion) to be valid when the IdP defines the start and endpoint. When establishing trust between systems, the IdP and SP systems must be synchronized because the SAML messages check that the system clocks on IdP and SP are synchronized. When the system clocks are not synchronized, trust cannot be established.
There are three possible scenarios when a credential (assertion) is not accepted by the Infinite BrassRing Platform.
Receiving a Not Yet Valid Assertion
If the IdP system clock is not synchronized with the SP system clock. When the NotBefore within the credential is set to a future time from the viewpoint of the SP, this error occurs. When the clocks are not synchronized, the SP does not accept the credential as valid. The Active Directory Federation Services (ADFS) allows SAML administrators to set the NotBefore value to a time in the past so the system clocks can synchronize.
Using the PowerShell tool, browse to Start → → Administrative Tools → → Windows PowerShell Modules and modify the RelyingParty (SP) with this command line:
At the PowerShell command prompt type:
Add-PSSnapin Microsoft.Adfs.PowerShell #Load up the ADFS PowerShell plug in
Get-ADFSRelyingPartyTrust –identifier “urn:party:sso” #Just to see what the values were
Set-ADFSRelyingPartyTrust –TargetIdentifier “urn:party:sso” –NotBeforeSkew 2 #Set the skew to 2 minutes
Select Enter.
NotBeforeSkew (ADFS 2.0)
You can also view more details on the ADFSRelyingPartyTrust ADFS 3.0 command here.
You can also view more details on the ADFSRelyingPartyTrust ADFS 2.0 command here
Prior to ADFS 2.0 the configuration could be configured differently.
Disable Encryption Temporarily
Sometimes trust cannot be established due to the encryption. You can temporarily disable the encryption by using the following command:
Using the PowerShell tool, browse to Start → → Administrative Tools → → Windows PowerShell Modules and modify the set-RelyingPartyTrust with this command line:
At the PowerShell command prompt type: set-ADFSRelyingPartyTrust -TargetName “TFIM SP Example” -EncryptClaims $False .
Select Enter.
SP Initiated Login Failure
If you encounter login failures with the SP initiated login process, you may need to add the SPNameQualifier property to the ADFS configuration. The value of this attribute is the entityID in the Infinite BrassRing Platform metadata file.
Note
For additional help, please consult to ADFS's troubleshooting document at Troubleshooting AD FS.
Replacing a Revoked Certificate
Abstract
Administrators receive email notification when it is necessary to revoke and replace a certificate. The email identifies the serial number of the certificate that requires replacement.
Navigating to the Inbound SSO
Talent Suite Administrator logs in to Talent Suite:
Selects the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Selects the Admin action on the Talent Suite navigation bar. The Administration page opens.

Browses to the Admin.
Opens hamburger menu and selects SSO → Inbound.

The Edit Inbound SSO Configuration page opens.
Adding a new Certificate
Administrators must find the location of the revoked certificate in order to add the new certificate. Administrator:
Locates the This certificate is revoked message. The location of this message determines where the Administrator need to place the new certificate. For example, if it is the signing certificate is revoked, the new certificate needs to be placed in the slot where the revoked certificate is located.
The Administrator opens the Show Details for the certificate to view and verify the certificate's serial number.
Drops the new certificate into the respective slot. Copy and paste can also be used to place the new certificate.
Selects Submit.
Note
If you encounter a parsing error when you submit the new certificate, see Resolving the SSO Certificate Parsing Error.
Working Around Lockout Scenarios
Abstract
When users encounter a lockout scenarios, there are work around that might resolve these isssues.
Forcing Infinite Talent management Solutions Login
When the option Authentication by identity provider only is enabled and the IdP login is not working as expected, the following actions force a non-IdP login:
You use the login URL you normally use but with the additional parameter sso.ts.login set to true, appending the ?sso.ts.login=true to the login URL.
You log in to Infinite Talent with an administrator who is not enabled for SSO.
SSO Single Sign-on Error Messages
Abstract
When SSO configurations present unexpected results, SSO Error message try to provide guidance in locating and correcting errors.
SSO Configuration Error Messages
When SSO configurations are unable to complete successfully, error messages generate and provide specific information to resolve those errors. The following error messages are the most commonly encountered during SSO configuration. Generally, error messages generate a code identifier.
HIWAA0002W
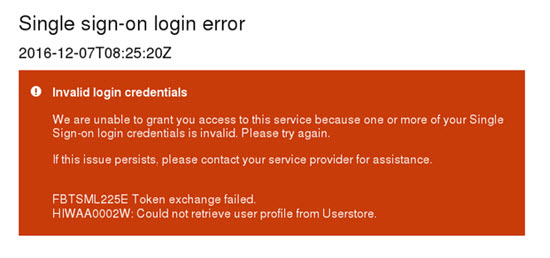
SAML message and general communication are working as expected although there is an invalid user error. The UserId provided inside of the SAML assertion does not match to any users within the configured User store. Verify that the server-side information includes the user name and then verify it within the configured User store.
FBTSTS019E
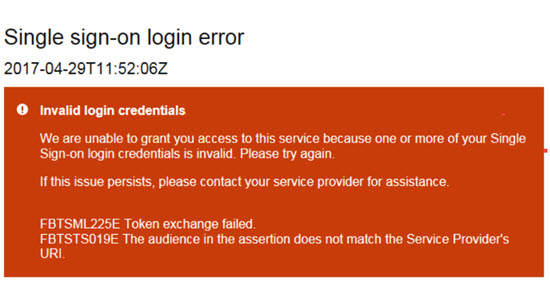
The received assertion includes a targeted audience that does not match the Identifier of the server. Use Kibana to search for the Audience element within the received assertion. This assertion might look like this: (<saml:Audience>https://stagingts.brassring.com/sps/inboundSSOStage/saml20</saml:Audience>)
The correct Audience for Staging is: https://stagingts.brassring.com/sps/inboundSSOStage/saml20 , and the correct Audience for Production is: https://ts.brassring.com/sps/inboundSSOProd/saml20
https://stagingts.brassring.com/sps/inboundSSOStage/saml20
Verify with the client and then change the Audience field to match the server EntitylD.
FBTSML236E
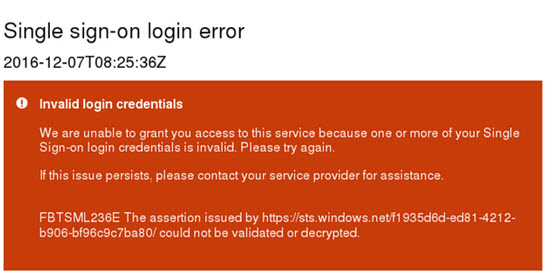
The received assertion could not be validated. Generally, this message means that either an incorrect certificate is stored inside of the customer configuration or the validity of the token has timed out. You can verify the assertion inside of Kibana by viewing the verify the verification Error on the server side. Often there is a mis-match between the certificate the client is using and the one visible within the SSO configuration page. If the certificate does not match, exchange it with the new one the customer is using.
FBTSML241E
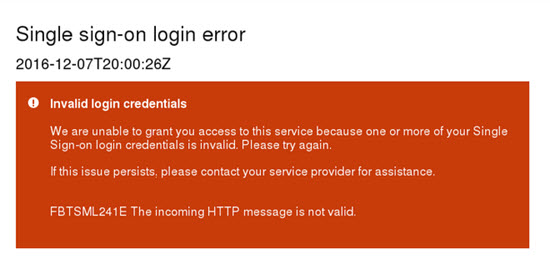
The processed request on the SAML endpoint is not valid. This error type could be caused by missing or incorrect parameters. You can use Kibana to view the access logs and check if the parameters match the Specification. If the RelayStateis visible, it needs to point to the application and not to the SAML endpoint.
FBTSML224E
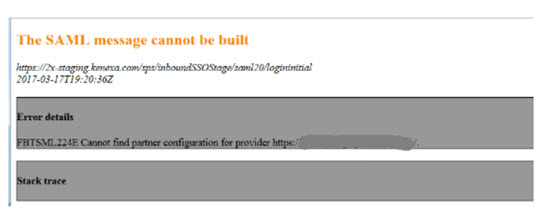
The SAML error message is that the SAML message cannot be built. This error can be caused by an incorrect configuration within the Inbound Page and the Identify Source page. Verify that the Entity Identifier and the Unique Name values match.
Working with the SSO Message Log
Abstract
The SSO message log allows Administrators to browse and filter messages that are related to SSO. For example, you will see a message after an SSO configuration has been successfully synchronized with the identity manager of the Infinite Talent environment .
Note
Only the 50 most recent message display in the message lot and messages are delayed for up to 30 minutes.
Navigating to the Message Log
Use these steps to browse to the message log:
Log in to the Infinite Talent as an SSO Administrator.
Selects the Application Launcher icon

to launch the Application Launcher navigation bar (if necessary).
Open the application launcher and select Admin.

Open the hamburger menu and select SSO/Message Log → Message Log.
The Message Log page opens.
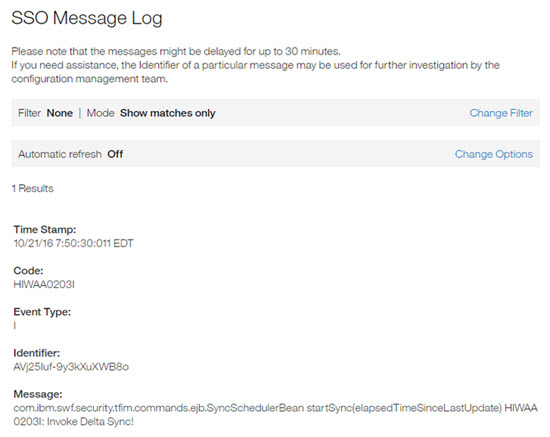
Filtering the Message Log
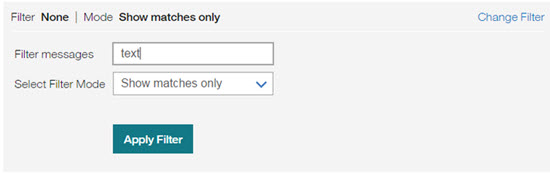
Administrators can filter messages by using the filter panel of the SSO message log. You open the filter panel by selecting Change Filter.
Selecting Change Filter opens the Filter dialog. Administrators can enter a filter string in the Filter messages text field and then select a filter mode:
Selecting Show matches only filter displays only messages that match the text string in the input text field.
Selecting Highlight matches displays all messages but highlights the messages that match the text string in the input filter. This selection keeps contextual message that might not necessarily match the text string in the input text field.
Select Apply Filter to view filtered messages.
Automatically Refreshing the Message Log
Administrators can also enable the message log refresh. Enabling the Automatic Refresh causes the message log to reload automatically every minute. Administrator:
Selects Change options on the Message Log page.
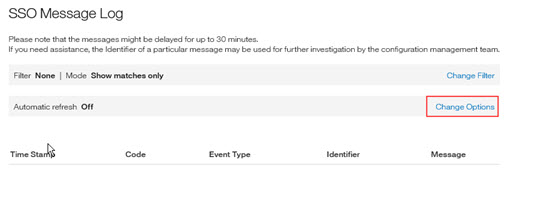
The Automatic Refresh dialog opens.

Selects the check box for Automatic Refresh.
Note
Enabling Automatic Refresh retains only the most current 50 messages. Older messages might be lost as new messages push out the older messages.
Collecting SAML Trace
SAML Trace
To further troubleshoot any SSO-related issues, it is suggested to collect the SAML trace related to your issue and to communicate the issue details to the Infinite Talent support team. This SAML trace contains important values for the key SAML attributes and greatly helps the support team to debug the issues. SAML tracers are available to most major browsers in the form of extension or add-ons such as SAML Tracer for Firefox, SAML Devtools Extension or SAML Chrome Panel for Chrome,, and Fiddler for Internet Explorer.
Consult your SAML tracer's documentation for how to capture and save a trace.